Zulucrypt: Difference between revisions
(→Try 2) |
|||
| (8 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
Zulucrypt allows you to open and create encrypted files and drives [https://www.google.com/search?sxsrf=ALeKk026QG9BbsZl0rNsBS9KmerMgczY_w%3A1602863734253&source=hp&ei=dsKJX6q8DJDYsAXHkpG4Cw&q=what+is+zulucrypt&btnK=Google+Search&oq=how+to+configure+nvidia+geforce+gtx+1650+super+on+linux+mint&gs_lcp=CgZwc3ktYWIQAzIFCCEQoAEyBQghEKsCMgUIIRCrAjoOCAAQ6gIQtAIQmgEQ5QI6DgguELEDEMcBEKMCEJMCOggILhDHARCvAToLCC4QsQMQxwEQowI6CAgAELEDEIMBOggILhCxAxCDAToFCAAQsQM6AggAOgQIABAKOgYIABAWEB46CAghEBYQHRAeOgcIIRAKEKABUMsQWOmzAWD8tAFoBnAAeACAAeQGiAGhS5IBDTExLjQ3LjMuMi42LTGYAQCgAQGqAQdnd3Mtd2l6sAEG&sclient=psy-ab&ved=0ahUKEwiqz4DcvLnsAhUQLKwKHUdJBLcQ4dUDCAk&uact=5]. | Zulucrypt allows you to open and create encrypted files and drives [https://www.google.com/search?sxsrf=ALeKk026QG9BbsZl0rNsBS9KmerMgczY_w%3A1602863734253&source=hp&ei=dsKJX6q8DJDYsAXHkpG4Cw&q=what+is+zulucrypt&btnK=Google+Search&oq=how+to+configure+nvidia+geforce+gtx+1650+super+on+linux+mint&gs_lcp=CgZwc3ktYWIQAzIFCCEQoAEyBQghEKsCMgUIIRCrAjoOCAAQ6gIQtAIQmgEQ5QI6DgguELEDEMcBEKMCEJMCOggILhDHARCvAToLCC4QsQMQxwEQowI6CAgAELEDEIMBOggILhCxAxCDAToFCAAQsQM6AggAOgQIABAKOgYIABAWEB46CAghEBYQHRAeOgcIIRAKEKABUMsQWOmzAWD8tAFoBnAAeACAAeQGiAGhS5IBDTExLjQ3LjMuMi42LTGYAQCgAQGqAQdnd3Mtd2l6sAEG&sclient=psy-ab&ved=0ahUKEwiqz4DcvLnsAhUQLKwKHUdJBLcQ4dUDCAk&uact=5]. | ||
=Open a File - Try 1= | =Why?= | ||
[https://en.wikipedia.org/wiki/TrueCrypt TrueCrypt] was abandoned and forked to become [[Veracrypt]]. | |||
The main VeraCrypt app has licensing issues and therefore isn't available directly in the Debian repos. | |||
You *can* mount a VeraCrypt volume on linux using zuluCrypt, which is licensed openly and available in the Debian repos | |||
=How= | |||
You can access a VeraCrypt volume using zulucrypt. | |||
This guide assumes you're using a Debian-based system (with <code>apt</code>). | |||
==Install== | |||
<pre> | |||
sudo apt-get install zulucrypt-gui | |||
zuluCrypt-gui | |||
</pre> | |||
==Open a File - Try 1== | |||
Open-> Volume hosted in a file -> filepath and select file. | Open-> Volume hosted in a file -> filepath and select file. | ||
| Line 13: | Line 34: | ||
[[Image:decrypt2.png|400px]] | [[Image:decrypt2.png|400px]] | ||
=Try 2= | ==Try 2== | ||
*Selected ose-veracrypt on the usb stick, whereas before I selected ose-veracrypt on desktop | *Selected ose-veracrypt on the usb stick, whereas before I selected ose-veracrypt on desktop | ||
| Line 21: | Line 42: | ||
[[Image:decrypt4.png|400px]] | [[Image:decrypt4.png|400px]] | ||
=Restoring Keyfile= | |||
*The shared passwords file is protected with another strong password, stored in user's personal keypass, AND a key file, stored on the encrypted folder which was just unlocked. | |||
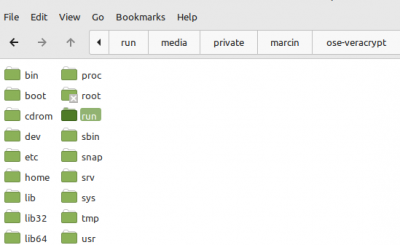
*The unencrypted folder directory is in /run/media/private/marcin directory | |||
[[Image:decrypt5.png|400px]] | |||
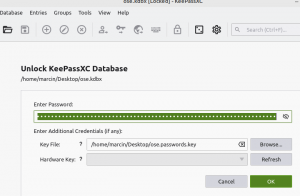
*Ideally, password and keyfile open the shared keepass file. But no luck, keepass database doesn't open: | |||
[[Image:decrypt6.png|300px]] | |||
=Restoring Keyfile 2= | |||
The above was done using backups, so possibly the password or keyfile was changed? | |||
But now, how to restore keys from a private and public key that is stored on an encrypted folder - | |||
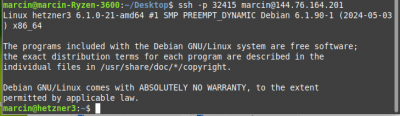
To restore your ssh key, copy the id_rsa and id_rsa.pub files onto your | |||
computer into the '.ssh/' directory on your home folder on your | |||
computer, and then run: | |||
ssh -p [secretportnumber] [username]@[ipaddress] | |||
Bingo! | |||
[[File:bingo.png|400px]] | |||
= See Also = | |||
* [[Maltfield_Log/2018_Q2#Mon_May_21.2C_2018]] | |||
* [[Veracrypt]] | |||
* [[Keepass]] | |||
* [[Pgp]] | |||
* [[LUKS]] | |||
* [[OSE_Server#sshfs]] | |||
* [[Backups]] | |||
* [[Server and Passwords Notes]] | |||
* [[Access Management Theory]] | |||
* [[Internet Security 101]] | |||
[[Category: IT Infrastructure]] | |||
[[Category: Software]] | |||
[[Category: Cybersecurity]] | |||
Latest revision as of 21:42, 11 April 2025
Zulucrypt allows you to open and create encrypted files and drives [1].
Why?
TrueCrypt was abandoned and forked to become Veracrypt.
The main VeraCrypt app has licensing issues and therefore isn't available directly in the Debian repos.
You *can* mount a VeraCrypt volume on linux using zuluCrypt, which is licensed openly and available in the Debian repos
How
You can access a VeraCrypt volume using zulucrypt.
This guide assumes you're using a Debian-based system (with apt).
Install
sudo apt-get install zulucrypt-gui zuluCrypt-gui
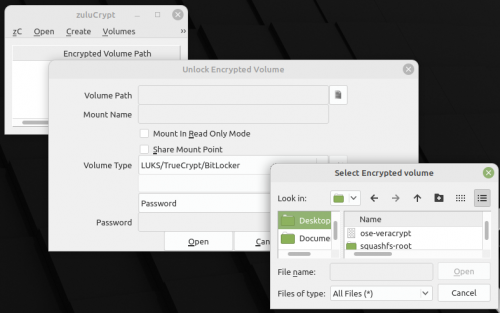
Open a File - Try 1
Open-> Volume hosted in a file -> filepath and select file.
After you select the file, such as ose-veracrypt, it will ask you for a password.
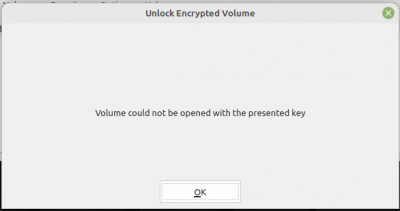
I typed in my strong password (selected the password option),and got:
Try 2
- Selected ose-veracrypt on the usb stick, whereas before I selected ose-veracrypt on desktop
- Also selected VeraCrypt instead of TrueCrypt etc, and bingo:
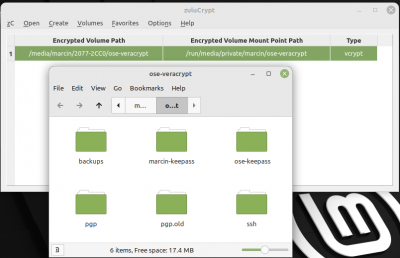
Restoring Keyfile
- The shared passwords file is protected with another strong password, stored in user's personal keypass, AND a key file, stored on the encrypted folder which was just unlocked.
- The unencrypted folder directory is in /run/media/private/marcin directory
- Ideally, password and keyfile open the shared keepass file. But no luck, keepass database doesn't open:
Restoring Keyfile 2
The above was done using backups, so possibly the password or keyfile was changed?
But now, how to restore keys from a private and public key that is stored on an encrypted folder -
To restore your ssh key, copy the id_rsa and id_rsa.pub files onto your computer into the '.ssh/' directory on your home folder on your computer, and then run:
ssh -p [secretportnumber] [username]@[ipaddress]
Bingo!